2.2 Network topologies, protocols and layers - Contents
In this chapter, you will learn:
Network topologies
The way networks are connected together is known as a topology. OCR J276 focuses on only Star and Mesh topologies, although there are other types of network topologies that can exist.
|
Note
|
Beyond GCSE Information The traditional way of networking computers was by using a Bus Network. All the computers are connected to a single central cable, which can only carry information. It first checks whether there is any traffic on the network, and then sends a message through the cable. A ring network has no central computer, and messages flow in one direction from one node to the next. It is difficult to extend the ring, and cabling costs can be high. The system is reliant on the reliability of the ring repeater. |

Above is an image displaying a star topology. Every computer is networked back to a switch. The server connects to this switch, which gives each node access to the server.
Setting up a star network is very intensive, regarding placing in the cabling. Additionally, the network is vulnerable to central hub failures. Internode connection is lost, when it comes to star topologies. This is a scalable solution.

Above is an image displaying a mesh topology. Each computer in a network connects to every other, creating a point-to-point connection between each device found on the network. The purpose; the mesh design is able to provide a high level of redundancy, in case of system failure.
It is very expensive and complicated when many machines are on the network, due to the amount of cables. It is difficult and complicated to install, and many of the connections serve no major purpose.
A partial mesh network is when some computers are connected together, but not every computer. This reduces cabling costs of a traditional mesh network.
WiFi
Wi-Fi is a facility allowing computers, and other devices to connect to the internet, or communicate with one another wirelessly within a particular area.
|
Note
|
Beyond GCSE Information The term does not mean, “Wireless Fidelity” as many would so assume. The Wi-Fi brand was created by Interbrand, a brand consultancy company specializing in corporate design and digital brand management. This was more diluted, as the original tagline for Wi-Fi was, “The Standard for Wireless Fidelity”. This served to confuse people and the WiFi branding even more. |
Wi-Fi works by sending radio waves at certain frequency bands (2.4GHz and 5.8GHz respectively), for the computers network interface controller (NIC) to receive. These transmissions can be intercepted by anyone in the range of the router. Within those frequency bands, are more specific frequency ranges. As long as the device and the transmitter are tuned to the same frequency, they can exchange information.

There are a lot of benefits to using WiFi:
-
Users can move around without being tethered by a cable
-
Easy to set-up, as no cables have to be run
-
Cheaper to set-up, as no cables have to be run
-
Convenient for users to use, again, as there are no cables to plug in
-
A lot of users can connect at one time
However, there are some downsides:
-
Speeds are slower, as it’s not transmitted over physical cables
-
Less secure than wired networks
-
Signal strength can affect speed
-
Signals can be obstructed by walls and other objects
-
Device has to support latest security standards
Transmissions are usually encrypted using a key that works from within WPA (Wi-Fi Protected Access). This is as wireless networks broadcast data in it’s entirety, so encryption is used to make it more secure.
The data is scrambled into cipher text, by using a master key created on the network. A handshake protocol is used to make sure each device has a valid master key, before transmission, so the device can decrypt this data.
Ethernet
Ethernet is a system for connecting a number of computer systems together, to create a LAN. It is a communication standard, so that many computer types can communicate with one another.
|
Note
|
Beyond GCSE Information The modern type of ethernet cable, uses a connector called RJ45; this cable type has wired for sending and receiving. This is the most common type of network cable in home networks. |
Ethernet started by using coaxial cables for communication, but has developed over time, and now uses Twisted Pair Cables, or Fiber Optic Cables.

Key definitions
IP Address
An IP address is a unique string of numbers separated by full stops that identifies each computer using the Internet Protocol to communicate over a network. Similar to a postcode to identify a house.
An example of an IP address is 192.168.0.1
|
Note
|
Beyond GCSE Information IPv4 and IPv6 differentiation is not part of the course. There are 4 billion unique IPv4 addresses, whilst with IPv6, there are 340 undecillion (or 340 billion billion billion billion) addresses. This is since IPv4 is stored in 32 bits, compared to IPv6s 128 bit size. |
MAC Address
MAC Addresses, or Media Access Control Addresses, uniquely identify a device on a network by identifying the network adapter that the device is using. This enables you to distinguish between different devices.
An example of an IP address is AA-32-G4-44-23-F1
It uses hexadecimal, 16 characters, in 2-character chunks.
Protocol definition
A protocol is a set of rules, which define the convention for communication over a network. These rules are used throughout the network, and also throughout the internet.
Key Protocols
There are many key protocols that exist for computer networks. The following are some key protocols to learn, and will then tie into further networking concepts:
TCP/IP (Transmission Control Protocol/Internet Protocol)
Defines how data is sent, transmitted and received over the internet. Defines four ‘layers’ for the transmission of data.
HTTP (Hyper Text Transfer Protocol)
Defines how multimedia webpages are identified, requested and transferred. Websites are generally constructed in HTML.
HTTPS (Hyper Text Transfer Protocol Secure)
Layer of security/authentication, on top of HTTP.
FTP (File Transfer Protocol)
Allows transfer of files between computer systems. Often used when sending data to web servers.
POP (Post Office Protocol)
Part of TCP/IP, used to send emails between systems.
MAP (Internet Message Access Protocol)
Part of TCP/IP, used to send emails between systems. Provides more facilities than SMTP. Emails are downloaded to device, and then deleted from server.
SMTP (Simple Mail Transfer Protocol)
Newer protocol to retrieve data from mail servers. Can ‘push’ emails to devices.
Network Protocols & Layers
Every device on the network has a network interface card, which contains a Media Access Control Address (MAC Address), which is the hardware address of the device on the network. This allows the communication of data (also known as the frame) to be transferred across the LAN.
IP addressing, on the other hand, is used to route packets on a WAN. This is a layer on top of MAC addresses.
IP addresses can be static or can be dynamic. If you reset the router, most the time devices will receive a new IP address.
|
Note
|
Beyond GCSE Information There are many different uses for a static IP address. It is used when a device requires an address that doesn’t change. For example, home file servers, or port forwarding (when you use a local computer to host a website), or sharing a printer over a network. |
Every router also has a WAN facing IP address, facing outwards. This can change, as it is assigned by the Internet Service Provider.
Within OCR, there are 4 different layers defined. These declare how data is sent over the network.
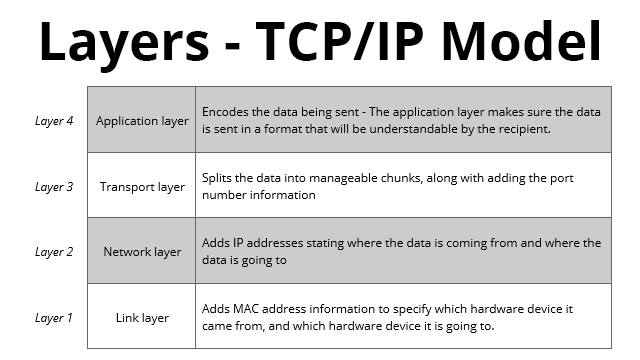
The layers are all handled via the TCP/IP protocol.
|
Note
|
Beyond GCSE Information Other models exist for layers; for instance, the OSI model defines 7 different layers. These include Application, Presentation, Session, Transport, Network, Data Link and Physical Link. |
Packet Switching
Packet Switching is a mode of transport over a network, where a piece of data is broken into smaller chunks, and transferred over the network. It is then reassembled at the other end. The process is as follows:
-
The data is broke up into smaller chunks. These smaller chunks are called packets.
-
Each packet is given a ‘packet number’. This identifies the order they are to be reassembled in.
-
They take the shortest route to arrive at their destination. This is usually the least bandwidth-heavy route.
-
A message will be sent to the original computer, to make sure it has been received.
-
However, sometimes packets do not arrive, or arrive incorrectly. It is then requested to be resent to the receiver.
-
Each packet is given a header.
-
When the packet is received, an error check is performed. The error check makes use of a check-sum number.
A packet header contains 3 key pieces of information; the source (where the packet originated from), the destination address, and the sequence number (so the receiver computer can reassemble the data into the correct order).
The TCP protocol handles splitting up the data, checking the transmission was successful, and sequencing the packets back into the correct order. The IP protocol, however, routes the individual packets into different directions.
The most famous packet switched network is the internet.
It contains billions of nodes and connections through with data packets can be transferred. When a router receives a data packet, it uses a table in its memory to look up the details of every other router which it is connected to. It then uses a set of rules, the IP protocol, to work out the fastest route in which to send the packet. Each packet will take its own path through the network and will be reassembled on the other side.
There are advantages to this method of communication over a wide area network:
-
It is robust; if one router fails or goes offline, there is usually another path available
-
It is efficient; packets are able to be sent even in times of high network traffic
-
Each packet has it’s own error checksum, meaning each packet can be checked individually
However, there are some disadvantages to this approach:
-
The packets travel along a long path, so there is no guarantee it will arrive in a timely manner. This is known as latency.
-
The packets arrive in a random order, so the computer has to reassemble the packets once they arrive on the client’s side.
-
If a packet is missing, it has to be resent, which causes delays and is troublesome.